Secure IoT networking with Soracom
|
Keep device traffic private and predictable
Design network paths that match your cloud and security architecture
Reduce complexity by shifting networking logic out of devices |

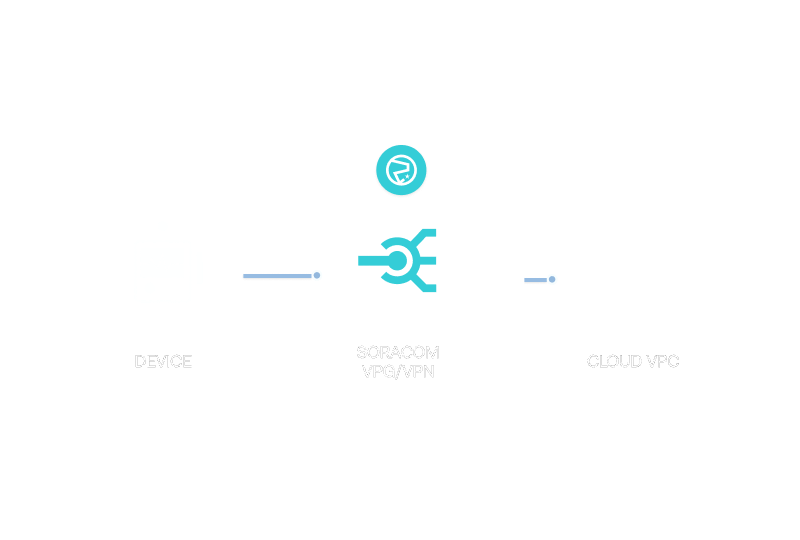
Build private, isolated data paths between your devices and your systems
Ensure every device communicates safely using private routes, encrypted tunnels, and controlled access paths.
Control how devices connect, how data moves, and who can reach it
Whether you’re connecting sensors in the field, industrial controllers in remote facilities, or finished products across multiple regions, securing your device traffic should not require custom carrier contracts or months of network engineering. Secure Networking Features give you control over how devices communicate, how data flows, and who can access it—without the operational friction of traditional private APNs or VPN hardware.
These capabilities work across regions and are designed to scale with everything from prototypes to nationwide deployments.
Getting started is simple
Explore our SOC2 compliant and IT-friendly options for private networking
Private network isolation without custom carrier contracts
Soracom secure networking services will allow you to isolate device traffic at the platform level—controlling which devices can talk to each other, where traffic is routed, and whether data ever touches the public internet.
This removes the need to procure a private APN from a single carrier or replace SIMs across your product line.
Example:
A logistics company can block all internet access and route traffic only into a private cloud environment, without requiring VPN clients on devices.
What teams normally struggle with
|
Private APN lead times
Device-side VPNs
Cross-carrier fragmentation
Secure server access
Managing inbound access |
Network tunneling for on-prem or cloud systems
Virtual private tunnel
Virtual Leased Line to Customer Network
Create an encrypted tunnel between the Soracom platform and your backend, eliminating the need for devices to run VPN software.
- Reduces device complexity
- Routes traffic securely over IPsec
- Works with private gateway configurations
Dedicated private line

Dedicated Line to On-Premise Network Infrastructure
Establish a fully private, non-internet path between your infrastructure and the Soracom platform as a leased-line alternative.
- Bypass internet entirely
- Consistent performance
- Ideal for regulated or mission-critical environments
Native routing to AWS hosted environements
Connect your AWS private cloud with no internet exposure
You can route device traffic into AWS environments using private VPC peering, Transit Gateway, or a virtual private tunnel—without exposing traffic over the public internet.
Example:
A smart-building platform can ingest data directly into their AWS VPC using private routing, with no internet exposure and no inbound firewall rules.
Granular control of network behavior
Traffic inspection and mirroring
Inspect or mirror packets passing through your virtual gateway for debugging or compliance.
- Diagnose unusual data usage
- Mirror traffic to analytics tools
- Validate device behavior
Learn about: Packet inspection and mirroring (Soracom Junction)
Device-to-device private networking
Place devices into the same virtual LAN for bidirectional communication, as if they were on a shared local network.
- Peer-to-peer communication
- OTA maintenance workflows
- Static private IP addresses
Learn about: Virtual LAN for IoT (Soracom Gate)
Additional capabilities used in secure network designs
Troubleshoot devices securely without risking static IPs or open ports
Open temporary, controlled access to devices even when they sit behind NAT, private gateways, or closed networks. Access sessions require no static IPs, no exposed ports, and no agent installed on the device—ideal for field diagnostics and secure maintenance workflows.
• Temporary one-time access
• Works with SSH, RDP, VNC, HTTPS
• No agent required
Route device data flexibly without changing your firmware
Use a single, consistent endpoint for every device in your fleet and manage routing centrally. This lets you switch destinations, redirect traffic, or fan out to multiple cloud services without updating firmware or touching devices in the field.
• One endpoint to manage
• Flexible data routing
• Reduces configuration errors
