What you’d build without Soracom Krypton
|
Burn credentials into firmware at the factory
Build a custom provisioning server
Develop one-off onboarding flows per deployment |
Soracom Krypton
SIM-based Device Provisioning and Authentication over Cellular
Provision devices securely without preloading credentials
Soracom Krypton uses the SIM as a hardware-based root of trust to provision devices into AWS, Azure, and other cloud platforms. It eliminates the need to embed secrets in firmware, manage certificates manually, or expose devices to insecure onboarding processes.
Automatically enroll devices into cloud services using SIM-based identity
With Krypton, devices authenticate to the Soracom platform using the security already built into the SIM card. Krypton then generates temporary cloud credentials or device certificates and delivers them securely to the device at boot. This removes the risk of hardcoded secrets, simplifies manufacturing, and ensures every device can safely register itself from anywhere in the world.
Why use Soracom Junction for your project?
Secure provisioning
Avoid hardcoded keys by issuing credentials on demand using SIM-based identity.
Simplify manufacturing
Reduce factory steps and eliminate the need to preload secrets or certificates.
Onboard anywhere
Devices can safely provision themselves in the field the moment they connect.
How it works
SIM-based secure authentication
Devices authenticate using the onboard SIM, creating a trusted identity without embedded secrets or certificates. Krypton uses this identity to request and deliver cloud credentials securely.
Automatic provisioning into AWS, Azure, and more
Krypton can generate AWS IoT Core certificates, AWS Cognito temporary credentials, Azure IoT Hub tokens, or custom onboarding payloads and deliver them to devices during startup.
Secure key delivery without firmware changes
Devices request credentials using a simple HTTPS or MQTT call to the Soracom platform. Krypton returns time-limited keys or certificates without requiring you to store secrets in firmware or update devices in the field.
Architecture and implementation
Krypton uses the SIM for identity, the Soracom platform for credential generation, and secure channels for delivery. When a device boots, it authenticates via Soracom Air or Arc, requests credentials from Krypton, and receives signed certificates or temporary tokens scoped to your cloud environment. This enables secure onboarding at scale without compromising firmware or requiring complex field procedures.
Enable Soracom Krypton and choose your provisioning method
Open the Soracom User Console and navigate to the SIM group where you want to automate device provisioning.
Enable Soracom Krypton in the group settings and select your provisioning mode, such as Bootstrap for initial identity exchange or Secure Provisioning for delivering configuration files, credentials, and device settings at first boot.
Krypton allows you to bind device identity to the SIM, removing the need for factory-time credential injection or manual configuration steps.
Setup guidance can be found in the Soracom Krypton documentation.
Configure your device to request identity or configuration from Soracom
Set up your device to make an HTTP request to the Soracom Krypton endpoint during its initialization process.
The request is authenticated using the SIM, allowing Soracom to return device-specific credentials, configuration files, or bootstrap information securely and automatically.
This eliminates the need for preloading credentials during manufacturing or handling secrets on the device.
Learn more in the Krypton device integration guide.
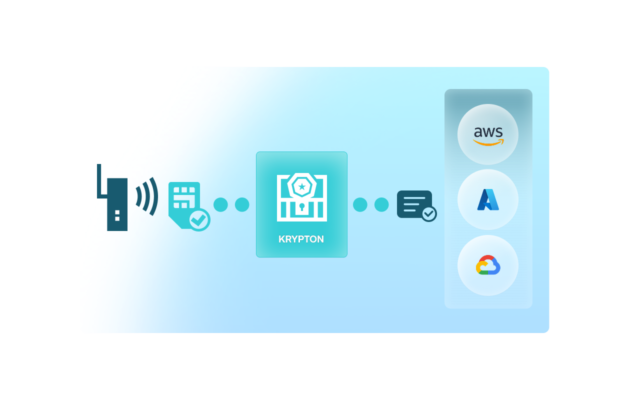
Use Krypton’s returned credentials to complete device onboarding
Once the device receives its Krypton-delivered payload, use the returned credentials or configuration to register the device with your cloud backend, enable secure communication, or complete initialization routines.
This ensures each device is provisioned with unique, SIM-bound identity and settings, without manual intervention or exposing secrets.
You can combine Krypton with services like Soracom Endorse or Funnel to automate secure onboarding all the way through cloud integration.
See backend integration patterns in the Krypton provisioning guide.
How Soracom Krypton works with other Soracom services
|
Use Krypton + Air for secure bootstrapping
Use Krypton + Beam/Funnel/Funk for cloud workflows
Use Krypton + Arc for secure non-cellular onboarding |